Reliable and available
Manage Product Content

Only with its use does meticulously created product content unfold its true value. That is why mediacockpit enables easy access and constant availability of product content.





Product Content Life Cycle
Well managed for increased productivity
Forget about time consuming searches
Marketing teams and creatives typically waste lots of time searching for relevant digital content and marketing materials that have already been created.
Connected information
mediacockpit manages both your product information and the associated creative content such as images, videos, documents or graphics. This close integration enables intelligent connections between your data making time-consuming searches a thing of the past.
Guaranteed availability
Without centralized data management, communication managers can never be sure that product content is up-to-date and approved for use.
Single Source of Truth
With mediacockpit as a single source of truth, marketers and product managers have full transparency over relevant product content and can effectively plan, prepare and control their next campaign or product launch.
Streamlined processes
Data quality also suffers quickly if data is not managed centrally. As a result, information has to be constantly touched up, wasting resources and resulting in added cost.
Excellent data quality right from the start
mediacockpit ensures optimal data quality right from the start and ensures that product information is complete and correct. This creates the basis for efficient processes around the creation, management and output of product content.
From searching and finding
Communication and marketing managers spend hours and hours searching for the right material, for example for the next campaign. Often, content that cannot be found is even created or purchased multiple times, which is extremely time-consuming and expensive.
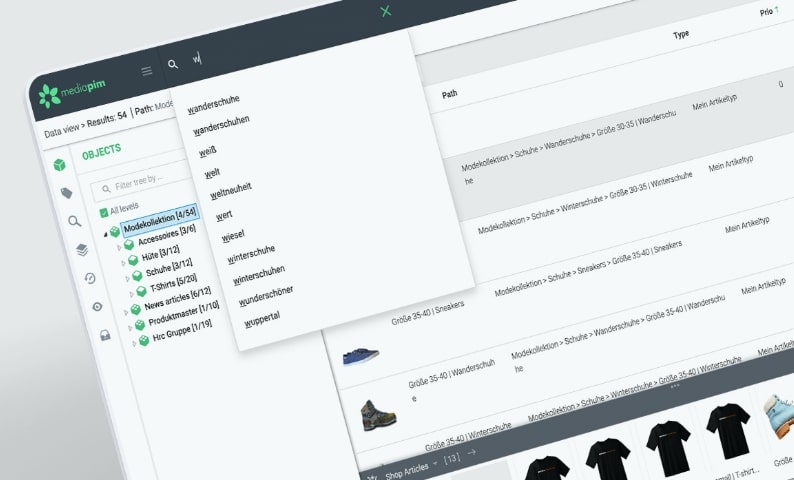
Everything at your fingertips thanks to Elastic Search
With mediacockpit, long searches are a thing of the past, because with its integrated Elastic Search search engine, users can immediately find the right images, videos, product content or documents. This saves time for more creative and strategic tasks.
Product content available to everyone at any time
Access to the truth of your data
Without central data management, important product information, editorial as well as digital content is often distributed throughout the organization, not equally accessible to all stakeholders and often available multiple times and in different versions. As a central platform for product content management, mediacockpit provides access to the one, current and correct data truth.
More efficiency
This transparency can save everyone who works with product information and digital content a lot of time and effort that they had to spend searching for relevant product content. Confidence in one’s own database also increases due to the reliability and validity of the information.
With mediacockpit, you have your entire product content life cycle reliably under control.

Access for all devices
High performance

Customer success

Priority support

Enterprise security

Continuous innovation
The professional, proactive and pragmatic approach, the permanent availability and the short response and processing times, and especially the comprehensive expertise as a software manufacturer combined with additional services – implementation and support – still convince me today that we made the right decision with Bertsch Innovation.
Marc Dawert
PIM Program Manager, Axalta Coating System
More insights
Accomplish more together
We believe in the value of collaboration and exchange. This applies both to our customer projects, from which we generate many valuable insights for our product development, and to our growing partner network, with an extensive range of which we support our customers in their digitization.


